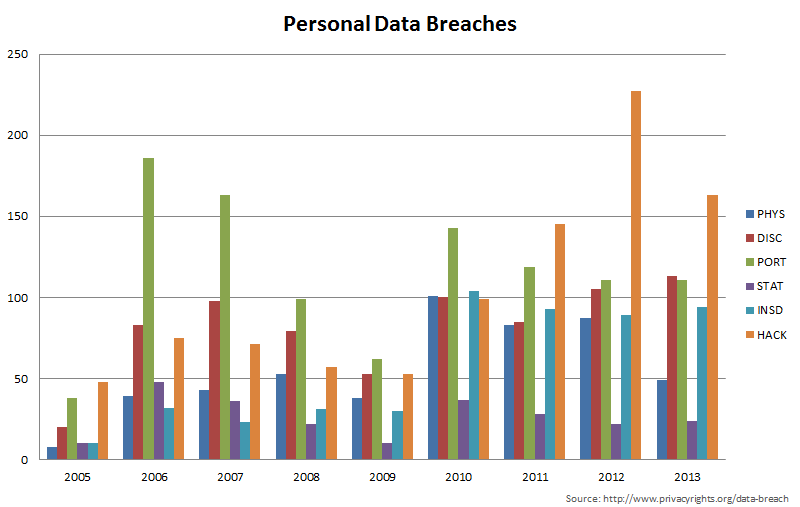
The Privacy Rights Clearinghouse, who is a nationally recognized consumer education and advocacy nonprofit dedicated to protecting the privacy of American consumers, collects reported personal data breach incidents and categorizes the breach into several different categories:
- Physical loss (PHYS) - Lost, discarded or stolen non-electronic records, such as paper documents
- Unintended disclosure (DISC) - Sensitive information posted publicly on a website, mishandled or sent to the wrong party via email, fax or mail.
- Portable device (PORT) - Lost, discarded or stolen laptop, PDA, smartphone, portable memory device, CD, hard drive, data tape, etc
- Stationary device (STAT) - Lost, discarded or stolen stationary electronic device such as a computer or server not designed for mobility.
- Insider (INSD) - Someone with legitimate access intentionally breaches information - such as an employee or contractor.
- Hacking or malware (HACK) - Electronic entry by an outside party, malware and spyware.
Aggregating this data year-over-year, you can examine the relative impact of these events and an upward trend in the number of reported incidents. The chart below graphs this data according to the above categories:
Its difficult to conclude that more data breaches are occurring today than in 2005 because there was less emphasis on reporting an incident 10 years ago. Additionally, one should not immediately conclude that the disproportionate increase in electronic hacking breaches indicates that personal data stored electronically is somehow less safe than maintaining it on paper. More importantly, this data illustrates that personal data can be lost or stolen in many ways and a company's data protection policy must address all possible scenarios to ensure data remains secure.
There are generally two ways to record personal data: paper or electronic. However, I tend to break electronic into two categories: local and remote. Local data is anything stored on a laptop, flash drive, smartphones, etc which generally has limited controls on access and physical location. Remote data is stored on a server specifically engineered to be located in a physically secure location, monitor access, and contains counter-measures for protecting against unauthorized access.
Using specific breaches from the Privacy Rights Clearinghouse, here are three examples to illustrate these main categories:
One of the reasons the number of reported hacking incidents is higher is because IT security professionals are deploying better monitoring technology to detect and report possible breaches. While prevention is clearly a goal, there will always be vulnerabilities. The point is to limit your susceptibility to data breaches and have mechanisms in place to detect and report a breach when one does occur.
Data policies that limit the use of paper and local storage mechanisms for sensitive data can significantly reduce a company's exposure to the potential of undetected data loss. Those two means of maintaining data have limited capabilities for monitoring a breach event. They also tend to require less talent and knowledge to actually acquire the data. On the other hand, well designed server-based data storage is specifically configured to employ safeguards against unauthorized access. Additionally, by keeping all this data in one known, secure location, one can reduce the effort required to monitor and protect the data.
A computer can be programmed to be infinitely vigilant. It will perform the same task over and over again without wavering forever. On the other hand, a human being becomes easily complacent and distracted. Its in those moments a mistake is made and security is potentially compromised. Constructing data protection policies that reduce the dependency on humans and increase the automation available in computer technology to ensure security will ultimately result in better control and protection of our sensitive personal information.
There are generally two ways to record personal data: paper or electronic. However, I tend to break electronic into two categories: local and remote. Local data is anything stored on a laptop, flash drive, smartphones, etc which generally has limited controls on access and physical location. Remote data is stored on a server specifically engineered to be located in a physically secure location, monitor access, and contains counter-measures for protecting against unauthorized access.
Using specific breaches from the Privacy Rights Clearinghouse, here are three examples to illustrate these main categories:
Paper Records
A packet of invoices was sent via the United States Postal Service. The package was damaged when it arrived at the USPS facility and some of the invoice pages were missing. The information in these missing pages included names, dates of birth, the last 4 digits of individuals Social Security number and the type of lab tests conducted.
Local Data
A flash drives containing patient names, dates of birth, information regarding individual diagnosis, individual treatment and insurance information were stolen from an employee's vehicle. The computer was encrypted but the flash drives were not.
Server Data
The company discovered that a server was infected by a malicious software that caused a breakdown in the server's security barriers allowing the hackers to obtain personal information. The information included names, dates of birth, ages, genders, addresses, race/ethnicities, medical record numbers, lab results all associated with research provided by individuals as part of research studies.Looking at these incidents, one should hopefully see that any means of recording, storing, and transmitting personal data is capable of being breached. Each mechanism has its own vectors of attack that thieves can use to acquire the data. What companies must do is employ measures to reduce the number of potential attack points to mitigate their risk of data breaches.
One of the reasons the number of reported hacking incidents is higher is because IT security professionals are deploying better monitoring technology to detect and report possible breaches. While prevention is clearly a goal, there will always be vulnerabilities. The point is to limit your susceptibility to data breaches and have mechanisms in place to detect and report a breach when one does occur.
Data policies that limit the use of paper and local storage mechanisms for sensitive data can significantly reduce a company's exposure to the potential of undetected data loss. Those two means of maintaining data have limited capabilities for monitoring a breach event. They also tend to require less talent and knowledge to actually acquire the data. On the other hand, well designed server-based data storage is specifically configured to employ safeguards against unauthorized access. Additionally, by keeping all this data in one known, secure location, one can reduce the effort required to monitor and protect the data.
A computer can be programmed to be infinitely vigilant. It will perform the same task over and over again without wavering forever. On the other hand, a human being becomes easily complacent and distracted. Its in those moments a mistake is made and security is potentially compromised. Constructing data protection policies that reduce the dependency on humans and increase the automation available in computer technology to ensure security will ultimately result in better control and protection of our sensitive personal information.