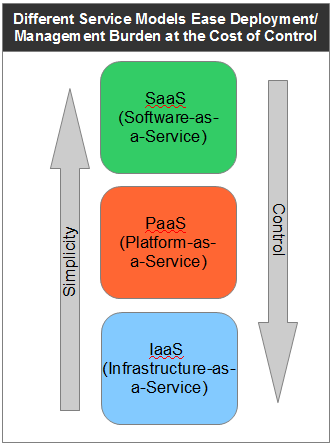
When we talk about the "Cloud", there are several types of service models you will see - infrastructure, platform, and software. Each model offers a different type of solution that meets specific business needs and creates varying levels of value. What model you use is based on several different factors including type of system, level of control, security, and regulatory compliance. Control tends to encompass all these areas since the controls a business places on its systems tend to correlate to both internal and external pressures to meet these specific requirements. Systems critical to business operations are generally kept on-premise either because they contain sensitive, proprietary business data and processes or the operating environment can't be effectively replicated outside the organization. As such, different cloud services may not satisfy all the requirements dictated by the organization, thus limiting a business from realizing the full benefit offered by certain solutions.
When we talk about the "Cloud", there are several types of service models you will see - infrastructure, platform, and software. Each model offers a different type of solution that meets specific business needs and creates varying levels of value. What model you use is based on several different factors including type of system, level of control, security, and regulatory compliance. Control tends to encompass all these areas since the controls a business places on its systems tend to correlate to both internal and external pressures to meet these specific requirements. Systems critical to business operations are generally kept on-premise either because they contain sensitive, proprietary business data and processes or the operating environment can't be effectively replicated outside the organization. As such, different cloud services may not satisfy all the requirements dictated by the organization, thus limiting a business from realizing the full benefit offered by certain solutions.At a minimum, a business might seek to move existing software off of in-house maintained hardware into a dedicated, private cloud solution. This is where IaaS (Infrastructure as a Service) provides the environment and staff to maintain the hardware used to run your software. Providers of these solutions include Amazon EC2 and Rackspace. An IaaS solution provides the maximum control over security, availability, and governance while still realizing the benefits of the cloud. The immediate value is less operations staff managing equipment and facilities. The downside is your IT organization is still responsible for most of the software, monitoring, and maintenance related to the deployed solutions.
A PaaS (Platform as a Service) goes a little further by offering an operating environment to deploy software solutions. These include Microsoft Azure and Google App Engine where you are provided a predefined stack to act as a container for your application. These solutions generally make it very easy to build software and run it in the cloud without spending any time or money configuring a hosting environment. From a value perspective, they allow you to retain an IT staff that focuses on creating solutions for your business and not how to deploy, scale, and monitor those applications. A PaaS will take care of many of these details automatically thus freeing you to invest in solving strategic business problems.
In the context of SaaS (Software as a Service), a business should require no IT staff to deploy, train, support, or maintain the solution. The provider takes care of all these details. As a business, you can recognize almost immediate value because the solution is available as soon as you sign up. There may be a learning curve to some systems, but compared to other implementations, you can jump ahead to training and usage on day one. There's two major drawbacks to a pure SaaS solution. One, they offer little control or visibility into the operations and management of security, availability, and reliability of the solution. Second, the system may provide little to no option to extend or integrate with other business systems. This silo effect greatly reduces the maximum value that can be obtained from a SaaS offering. While a business may enjoy the immediate benefit of the system, as time goes on, the system is unable to grow beyond the confines of the solution itself preventing a business from realizing additional improvements in efficiency available through customization.
Providers are recognizing this short-coming and building APIs to their solutions which offer organizations an opportunity to integrate other business systems with a SaaS solution. This ability to extend a solution enables an organization to continue to optimize business processes and increase the value of all their business systems. While this value is not immediately obtained, a clear path exists to realize the potential available in the system.
A new trend solution providers are exploring is going beyond the API and offering specific PaaS-like solutions tailored specifically to the system they provide. Typically, the environment enables deploying custom solutions built around their API to enable a faster path to realizing value within the solution. These hybrid approaches are blurring the lines between service model providers and may squeeze out generic offerings in favor of solutions tuned to the needs of the different business systems being used. The overall value a organization can achieve through these solutions is higher than that of any one stand-alone offering since ecosystems typically begin to evolve around these platforms that a business can turn to for finding best-in-class solutions that can be dropped in and immediately add benefit to the business.
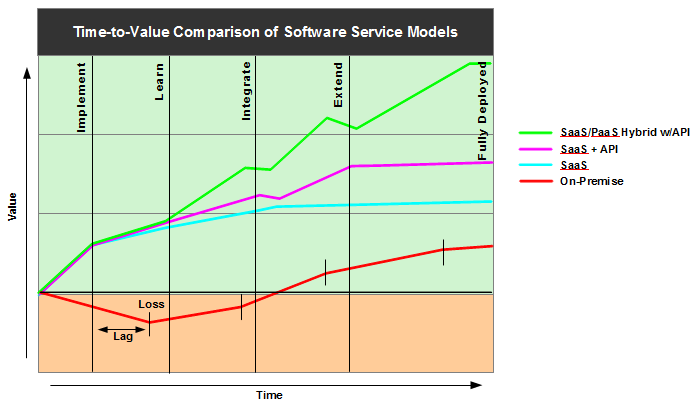
The graph shows several variations of a SaaS solution verses buying, installing, and running a solution in-house. The greatest difference in value is visible in the upfront cost of a on-premise solution. At the point of purchase, no value is created by the solution - just the potential for value. In comparison, most SaaS solutions are pay-for-use which immediately returns value to the organization by not creating a significant drain on capital. Additionally, since the on-premise solution must be deployed within the organization, there's a time lag before any value can start to be realized. Again, a SaaS solution avoids this problem and in most cases, an instance is provisioned and available for use in less than a day, if not a few minutes or hours. The remaining series on the graph show that SaaS solutions with API and platform options provide greater opportunities for deriving continued value from the solution. Devoid of these options, the value line levels off as a business fully adopts the solution into its operations.
Choosing a solution for your organization requires an understanding of your business's requirements and tolerance to loss of control. Clearly, when those factors align with a cloud-based solution, a company can realize significant value in a short period of time. Additionally, as the focus shifts from running everything internally, business can utilize their IT organization more efficiently to solve specific business needs.